Crack Me
Recon
Using jadx-gui to open CrackMe.apk, under the file com.SekaiCTF.CrackMe notice that MainActivity is extended from ReactActivity, hence we can know that this application is written with react native.
React Native
React Native Application Analysis
…
Navigate to the newly created ReactNative folder and locate the assets folder. Inside this folder, you should find the fileindex.android.bundle, which contains the React JavaScript in a minified format.
From HackTricks, we can know that the code for this application is stored in assets/index.android.bundle.
First, use apktool to decode CrackMe.apk in order to extract the source code for further analysis.
apktool d CrackMe.apk
Then, decompile index.android.bundle with react-native-decompiler.
npx react-native-decompiler -i ./index.android.bundle -o decompile
Login Panel
Run the application in Android Studio Android Emulator to find the possible place for hiding flag, we can see that only one CRACKME button is in the home page, which leads us to a login panel.

Search for keywords (e.g. CRACKME, account, admin) from the login page in decompiled code to find the possible authentication function, when searching for admin, the admin’s email and validatePassword function showed up.
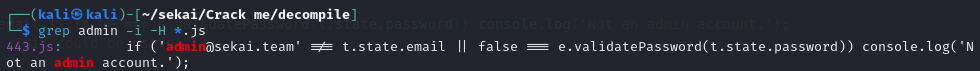
Take a closer look at 433.js, we know that the admin’s email is admin@sekai.team and password is encrypted by AES with KEY and IV from 456.js.
// 433.js
if ('admin@sekai.team' !== t.state.email || false === e.validatePassword(t.state.password)) console.log('Not an admin account.');
else console.log('You are an admin...This could be useful.');
var s = module488.getAuth(n);
module488
.signInWithEmailAndPassword(s, t.state.email, t.state.password)
.then(function (e) {
t.setState({
verifying: false,
});
var n = module486.ref(o, 'users/' + e.user.uid + '/flag');
...
e.validatePassword = function (e) {
if (17 !== e.length) return false;
var t = module700.default.enc.Utf8.parse(module456.default.KEY),
n = module700.default.enc.Utf8.parse(module456.default.IV);
return (
'03afaa672ff078c63d5bdb0ea08be12b09ea53ea822cd2acef36da5b279b9524' ===
module700.default.AES.encrypt(e, t, {
iv: n,
}).ciphertext.toString(module700.default.enc.Hex)
);
};
// 456.js
var _ = {
LOGIN: 'LOGIN',
EMAIL_PLACEHOLDER: 'user@sekai.team',
PASSWORD_PLACEHOLDER: 'password',
BEGIN: 'CRACKME',
SIGNUP: 'SIGN UP',
LOGOUT: 'LOGOUT',
KEY: 'react_native_expo_version_47.0.0',
IV: '__sekaictf2023__',
};
exports.default = _;
First, write a script to get the KEY and IV after parsing.
module456 = require('./456.js')
module700 = require('./700.js')
var t = module700.default.enc.Utf8.parse(module456.default.KEY),
n = module700.default.enc.Utf8.parse(module456.default.IV);
console.log(t)
console.log(n)
Then use python to decrypt the password, which is s3cr3t_SEKAI_P@ss.
from Crypto.Cipher import AES
from Crypto.Util.number import long_to_bytes
key_words = [1919246691, 1952411233, 1953068645, 1600485488, 1868527205, 1920166255, 1851733047, 774909488]
key = 0
for i, k in enumerate(key_words[::-1]):
key += k << (i * 32)
iv = 0
iv_words = [1600090981, 1801546083, 1952854576, 842227551]
for i, v in enumerate(iv_words[::-1]):
iv += v << (i * 32)
cipher = AES.new(long_to_bytes(key), AES.MODE_CBC, long_to_bytes(iv))
print(cipher.decrypt(bytes.fromhex("03afaa672ff078c63d5bdb0ea08be12b09ea53ea822cd2acef36da5b279b9524")))
Unfortunately, after successfully login as admin, only a pop up window with text already seen in source code showed up, no flag or anything interesting.
Going back to the source code, notice var n = module486.ref(o, 'users/' + e.user.uid + '/flag'); may be where the flag is stored, after digging into getAuth, signInWithEmailAndPassword, we can see that there exist a firebase database and credentials in 477.js.
// 477.js
var c = {
apiKey: 'AIzaSyCR2Al5_9U5j6UOhqu0HCDS0jhpYfa2Wgk',
authDomain: 'crackme-1b52a.firebaseapp.com',
projectId: 'crackme-1b52a',
storageBucket: 'crackme-1b52a.appspot.com',
messagingSenderId: '544041293350',
appId: '1:544041293350:web:2abc55a6bb408e4ff838e7',
measurementId: 'G-RDD86JV32R',
databaseURL: 'https://crackme-1b52a-default-rtdb.firebaseio.com',
};
exports.default = c;
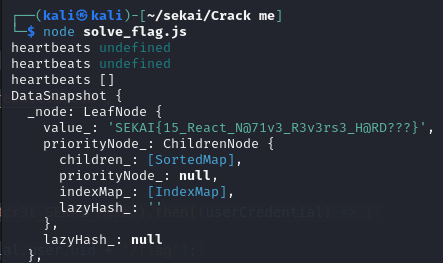
Write another script to connect to firebase and get the flag.
import { initializeApp } from 'firebase/app';
import { getAuth, signInWithEmailAndPassword } from "firebase/auth";
import { getDatabase, ref, onValue } from "firebase/database";
const firebaseConfig = {
apiKey: 'AIzaSyCR2Al5_9U5j6UOhqu0HCDS0jhpYfa2Wgk',
authDomain: 'crackme-1b52a.firebaseapp.com',
projectId: 'crackme-1b52a',
storageBucket: 'crackme-1b52a.appspot.com',
messagingSenderId: '544041293350',
appId: '1:544041293350:web:2abc55a6bb408e4ff838e7',
measurementId: 'G-RDD86JV32R',
databaseURL: 'https://crackme-1b52a-default-rtdb.firebaseio.com',
};
const app = initializeApp(firebaseConfig);
const auth = getAuth();
signInWithEmailAndPassword(auth, 'admin@sekai.team', 's3cr3t_SEKAI_P@ss').then((userCredential) => {
const db = getDatabase();
const starCountRef = ref(db, 'users/' + userCredential.user.uid + '/flag');
onValue(starCountRef, (snapshot) => {
const data = snapshot.val();
console.log(snapshot)
});
})
Miku vs. Machine
Problem Description (from sekai CTF 2024)
From the problem description, we can know that stage time for each singer (denote \(t\)) is \(\frac{m\times l}{n}\), we can simply choose \(l = n\) to let \(t\) be an integer, then, in this case \(t = m\).
Since \(l = n \leq m = t\), each singer’s stage time is guaranteed to be equal or longer than one show, which means the solution can be arrange each singer’s stage time continuously, only split it when exceeds the show length, and change to next singer after the previous singer’s show time is completed.
The corresponding python solution is as follow.
# get input t
t = int(input().strip())
# t test cases
for _ in range(t):
# get input n, m
n, m = map(int, input().strip().split())
# output l, which equals to n
print(n)
# starts from first singer
cur = 1
remaining = m
# loop through each show
for _ in range(m):
# case1: current singer's remaining stage time is not less than a single show time
if remaining >= n:
# assign whole show to the current signer
print(f"0 {cur} {n} {cur}")
remaining -= n
# switch to next singer if the current singer finishes
if remaining == 0:
cur += 1
remaining = m
# case 2: current singer's remaining stage time is less than a single show time
else:
# finish current singer's stage time and remaining show time to next singer
print(f"{remaining} {cur} {n - remaining} {cur + 1}")
cur += 1
remaining += m - n
